This website is an independent observer of Maidsafe and Autonomi's journey to launch.
The latest Updates
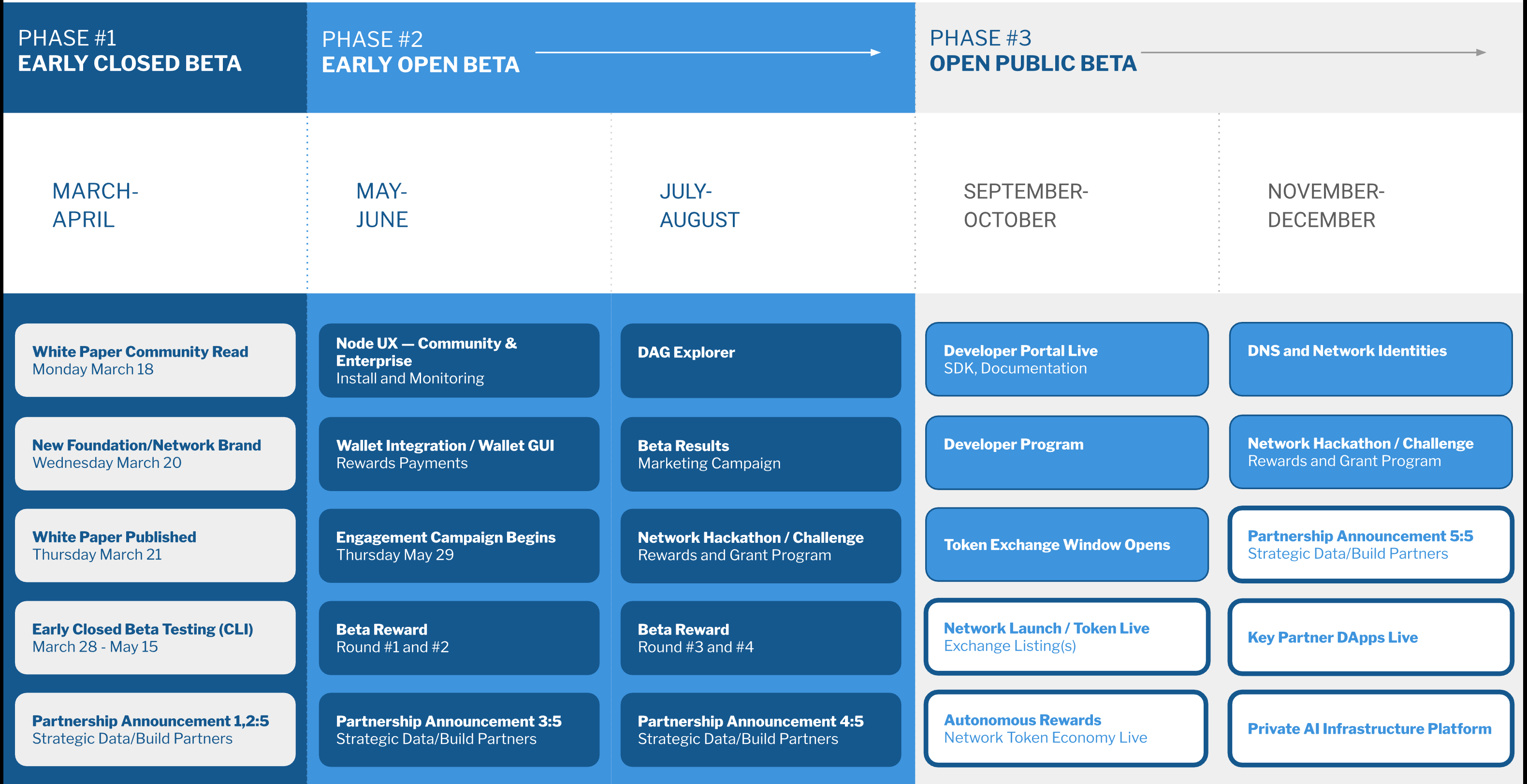
- Rebranding to “Autonomi,” new website and whitepaper – see also Section 10 below. The logo is an ant’s head. (March 21, 2024)

The SAFE Network project is complex. It has been under development since 2006. This wiki collects information to make the SAFE Network project more accessible. The best place to read about the latest developments as they happen is the Safe Network Forum.
Outline
1. Introduction (<-Click Here)
If you want to find out more about SAFE Network or start contributing, this should help you get started.
- Beginner intro
- Intermediate intro
- Expert Level intro
- Sourcecode
- Packaging
- RFCs and Discussion
2. Goals of the SAFE Network
Understand what SAFE Network is really about, and why it’s worth the wait.
- SAFE Network Core Goals (unofficial)
- SAFE Network Non-Core Goals (unofficial)
- Benefits
- Roadmap and Beyond
3. Architecture and Implementation
This section will be an attempt to give an accurate overview of the architecture. (Warning: This section is now very much out of date.)
- Place in OSI Reference Model
- SAFE Network Overlay Network
- Basic Facilities
- Transport Protocol for P2P
- IETF QUIC Introduction
- MDSF Lib quic-p2p
- Routing
- Kademlia Routing Introduction
- XOR Distance
- MDSF Lib routing
- Parsec
- Vault
- Gossip Protocol
4. Mechanisms
In this section, we will try to separate out and have a closer look at the mechanisms that will keep the SAFE Network working as intended.
- Security Aspects
- Mechanisms to Ensure Security
- Other Operating Mechanisms
- Forum topics on studies
5. Economics
This section will consider the Economics of SafeCoin on the network.
- MAID pre-launch
- MAID and SafeCoin at launch
- SafeCoin
6. Dealing with MAID and SafeCoin
Handling MAID and SAFE Network tokens is more complicated than dealing with cash. This should be a guide to make things easier.
- What is MAID
- What is SafeCoin
- Exchanges trading MAID
- Storing MAID offline
- eMAID conversion
7. Hardware Guide for Miners
- Node characteristics
- Hardware ideas
8. Software Guide for Users
(how to start using apps.)
9. App Dev Guide for Developers
(how to start app software development)
10. Labs for Builders
- Tools
- How-to’s
- Community Testnets
Appendices
- A. Unofficial FAQ
- B. History and Timeline
- C. People
- D. Corporate Organization
- E. Patents and Trademarks
- F. Related, or Similar Projects
- G. Lists of Resources
- H. Philosophy
updated: 20240308
The base content was taken from the MaidSage SAFE Network Wiki which was operated as a docuwiki at maidsage.com, 2019-2024. Ideanist.com will take over curation. The entire history of maidsage.com remains available on Github (and also the internet archive - check earlier versions to view missing content from latest crawls).